- Joined
- Aug 26, 2023
- Messages
- 7,665
- Reaction score
- 12,216
- Location
- US
- Gender
- Male
- Political Leaning
- Slightly Liberal
Sure. Have them hire me and give me admin access and I’ll see what I can put together. I’d also like to point out that one of the message recipients was in Russia. Those messages while encrypted are open for grabs to Moscow. Can they decrypt them? It is possible and there are potential ways hence why this isn’t allowed by policy.If you are claiming that Signal has been exploited by a MiM attack in the message flow, do please support that.
So you think it would have been just fine if they put that on Twitter before or during the attack. No. I think you have your answer.There's more to consider in that than just your declaration of it being so.
I did skim it. You are claiming the contrary. Which part of the policy did you want to highlight?
The date wasn't specified.
Targets were not specified.
Locations were not specified.
Routes were not specified.
Specific units were not specified.
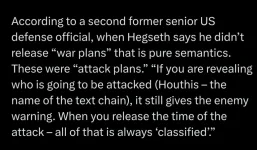
With out those, you really don't have much an 'attack plan' or 'war plan', or at least you have a next to useless one, which is next to useless for anyone who would try and defend against this plan's execution - no specifics.
Same argument to the previous silliness.
Signal is a public network. I don’t care that you don’t understand that.It wasn't 'on public network', it was in a private strongly encrypted chat app with a mistaken invitee, apparently.
I agree youre being political. We both know exactly how you’d react if this was done by Biden. Do you have anything new to add? At this point you’re just circling the drain with desperate arguments that don’t make any sense.Given the above, it appears that far more is being made of this than is really there, and I suspect that it is being made more of is strictly political.
Last edited: